The Better Mousetrap
Making the perfect e-mail client seems like the build-a-better-mousetrap challenge of our day. Every year or so it seems there’s another amazing e-mail client released by a startup, that says it has ‘reimagined’ or ‘reinvented’ e-mail and how to use it. Some examples include Sparrow (launched in 2011, bought by Google and discontinued in 2012) and Mailbox (launched in 2013 and bought a month later by Dropbox, and announcement of its imminent retirement just this month). This is kind of ironic considering the move away from e-mail to other messaging services, particularly real-time services, such as Slack and Whatsapp.
Recently, perhaps due in part to the imminent shut down of Mailbox, another e-mail app called Polymail has been receiving a lot of hype. It is already the fourth most up-voted product on Product Hunt, and it hasn’t even launched yet. Seeing the latest e-mail-mousetrap launch reminds me about one of the inherent security problems all of these applications encourage.
A Question of Protocol
All of these apps rely primarily on the IMAP e-mail protocol (short for Internet Message Access Protocol). That makes a lot of sense as it keeps most of the e-mail management on the server, and allows app developers to release both desktop and mobile clients that can both share the same e-mail, including read status and folder structure. Many of the largest e-mail providers like Gmail, Yahoo, iCloud, and Outlook.com (the service formerly known as Hotmail) support IMAP, so these e-mail accounts are generally supported by these new e-mail clients.
In the old days, most e-mail was served up using a different protocol, POP, short for Post-Office Protocol (technically it is POP3, and IMAP is actually IMAP4). The truth is that both POP and IMAP date back to the 1980s. POP is only a couple of years older than IMAP, although IMAP received more ongoing attention in the 1990s. There are a lot of differences between POP and IMAP, but the main difference is that when you use POP, all of your messages are downloaded to your e-mail client, and then deleted from the server, while IMAP downloads a local copy, but leaves all the e-mail on the server.
Keeping e-mail on the server has many advantages, such as having a backup of your e-mail on a remote server, and allowing your phone, tablet and desktop to all access your e-mail. There are some minor problems with keeping your e-mail on the server, such as running out of server space (depends on your e-mail provider). One problem that is usually overlooked, however, is that if your e-mail is stored on the server, your e-mail is accessible at all times by hackers and the government. Let’s take a look at these two scenarios.
Scenario One: Hackers
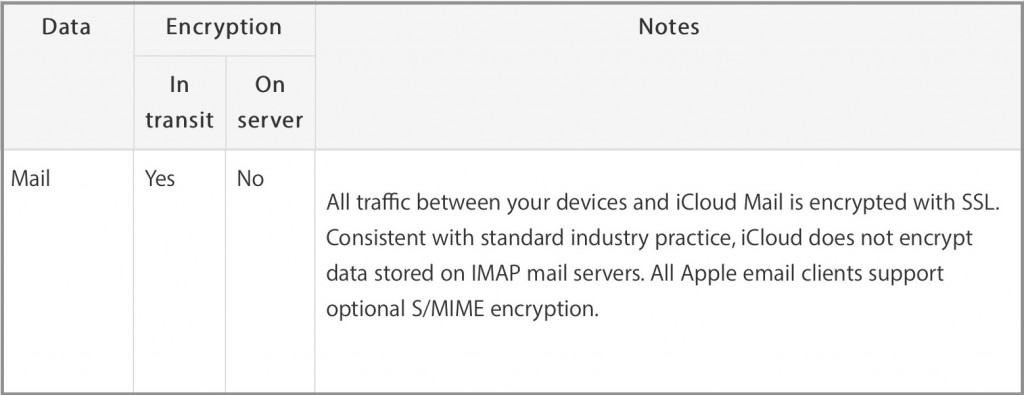
In the old days e-mail was never encrypted. Nowadays more and more companies are trying to insure it is encrypted when in-transit between servers. Google offers an interesting view of their attempt to encrypt e-mail in transit to different providers, showing which companies they receive and send e-mail to that are fully encrypted, and which are not. This in-transit encryption prevents, or at least greatly lowers, the ability of third parties (criminal or government) to intercept your e-mails while they are traveling between servers, or from a server to your client device. That’s great, but there’s one problem they don’t usually talk about, which is that the e-mails are stored unencrypted on the server itself. Apple actually points this out in their iCloud security and privacy overview:
Now I’m sure most major e-mail providers have amazing security, but nothing is a guarantee. How many times have you received spam from a friend whose account on a major e-mail provider or social network had been hacked? I still remember the first time I received the ‘I’m stranded in X and need you to wire me money’ scam. If your e-mail is online, it’s available to those who can access the server. That could be high-level hacks that compromise the entire server, or simple hacks like guessing your password. Check out HaveIBeenPwned.com to search a database of over 250 million username/password credentials that have been hacked and leaked online and you may find your e-mail address there. Do you use the same password on multiple sites? how about the same password for your e-mail and for online sites? That’s a big no no, but when the most common password on the Internet is ‘password’ security isn’t a major concern for many.
Even if you use strong passwords and use different passwords on different sites, however, there are more intricate methods for gaining access to e-mail without having to hack the server directly. Take for example the teenager that gained access to the personal e-mail account of John Brennan, the director of CIA. He did a reverse-lookup of Brennan’s phone number, determined its provider (Verizon), and called Verizon pretending to be a Verizon technician. This is called social engineering, and it’s basically hacking without a computer. The teenager managed to get enough information from Verizon to then call AOL and reset the password on the e-mail account. This was the director of the CIA.
Scenario Two: The Government
Sure, everyone knows the NSA is listening. Edward Snowden’s revelations about the NSA have been news fodder for years. One of the most troubling images released by Snowden via The Guardian was this slide from a presentation on NSA’s PRISM electronic surveillance program:
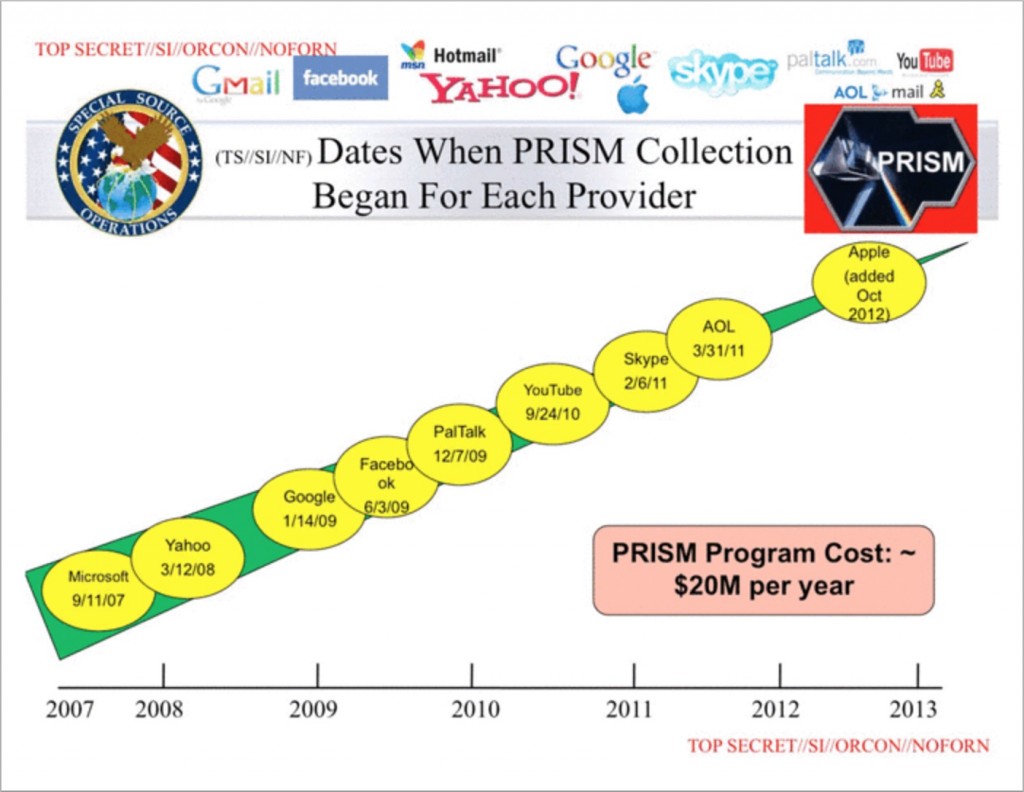
The slide seems to suggest at which point each of these services were compromised by the NSA. Whether these services were hacked by the NSA or were given access by the providers isn’t shown. That distinctions is really irrelevant, it would seem. Does this mean that the NSA can read all of your Gmail, Yahoo and iCloud e-mails? That’s not clear, but it doesn’t seem that is what they mean. It is possible that this slide merely means that the NSA is capable of intercepting all e-mails being sent and received by these servers. For example, they connect to the data pipes in between the hosting location and the Internet provider they use. The NSA can just listen in to everything coming and going, and doesn’t need to access the servers at all. That might have been the impetus for Google’s increased focus on in-transit encryption as mentioned above.
Now you might say that a lot of these programs were shut down and are not active. That’s also irrelevant. You know why? Because you don’t need to be the NSA to access e-mails stored on servers. You don’t even need a warrant. You’re probably thinking that’s crazy, and of course law enforcement agencies would need a warrant to access your e-mail on the server. NOT. TRUE. The Electronic Communications Privacy Act of 1986 (ECPA) defines e-mail on a server that is more than 180 days old as abandoned. This dates back to a time when everyone used POP or a proprietary protocol to download their e-mails, and storage was so expensive that keeping everyone’s e-mails on the server seemed absurd. Back then the assumption was you could download your e-mail and then the server would delete it to make room. The problem is that this antiquated definition is still the law of the land, and a law enforcement agency can ask for all e-mails older than 180 days and doesn’t need a warrant to do so. That’s not to say e-mail providers haven’t fought against this definition, but the law is on the government’s side until it gets changed. Meanwhile, if the government wants to take a look at the e-mails you’ve downloaded to your computer, they need a warrant. So if you store your e-mails remotely (using IMAP), the government can simply ask for them with little justification. If you download all your e-mails (using POP) then the government needs to go to a judge and get a warrant to search your computer, which they obviously need to get from you physically. If an e-mail provider hands over all your e-mails to a law enforcement agency, how would you know it even happened?
The interesting thing then is that using the older POP protocol, you are in many ways more secure than if you use IMAP. If you’re using in-transit encryption, which both IMAP and POP support, then the only e-mails accessible to government agencies when they approach an e-mail provider are what are sitting there in between downloads to your client. It’s usually a pretty good bet that those are less than 180 old, which means the government cannot get access to any of your e-mails if you use POP, without a warrant.
Sure all of this is theoretical. I don’t assume anyone reading this is being pursued by law enforcement. That said, any loophole is exploitable. Just ask John Brennan.
Then What?
The obvious answer to e-mail security is to encrypt all e-mails all the time. That, however, is harder than it seems. First, you can’t force other people to send you e-mails that are always encrypted. Second, even setting up encryption for all of your outgoing e-mails is incredibly difficult. It doesn’t feel like so long ago that Phil Zimmerman had to publish the code to his PGP encryption software in a hard-bound book and put it up for sale, in order to allow it to be exported outside the US under the First Amendment. The problem at the time was that strong encryption was considered a munition under US law, and exporting it to many countries was illegal. Anyone with a copy of the book could rip off the cover, separate the pages, and then scan the pages and generate the source code. A project to do just that outside the US was set up to stay up to date with new versions, called the PGPi scanning project. Nowadays, those laws are more relaxed, and no scanning in foreign countries is required. It’s not a secret sauce anymore. Getting strong encryption code out into the wild was only part of the problem, however. The bigger problem turns out to be a question of how easy encryption is to use.
Many people have tried to make encryption easier to use so more people would use it, but no one has really succeeded. Phil Zimmerman himself advised Hushmail, and co-founded Silent Circle, both of which could be described as attempts to make encryption more accessible. More recently two other efforts are perhaps more interesting.
Will Ackerly, who used to work at the NSA, launched Virtru, a company that piggybacks on existing e-mail services like Gmail and adds strong encryption. Some of the things Virtru allows beyond encryption are the ability to allow or disallow an e-mail from being forwarded, and the ability to revoke an e-mail (i.e. delete it from the recipient’s computer) at will, or automatically after a set period of time. Additionally, recipients of encrypted e-mails don’t need to install special software to read messages sent via Virtru. Virtu currently offers Chrome and Firefox plug-ins for web-access to services like Gmail, and offers a plug-in for Outlook on the Windows desktop. They also offer iOS and Android apps. Virtru tries to be a simple end-to-end solution for secure e-mail, and it does seem to do things very well.
Another startup, Keybase, was founded by the former founders of online dating site OKCupid. Founding a dating site might not sound like the right pre-requisite for bringing encryption to the masses, but besides building OKCupid based on complex mathematical matching algorithms, they also managed to sell their company to Match.com for $50 million in cash. As proven entrepreneurs, they managed to convince the right people, and raised $10.8 million from major silicon investors just to get started on the problem. The idea behind keybase is to link your cryptographic key with your various social media profiles, making it much easier for people to locate your public key and communicate with you. For example, you might link your Facebook, Twitter, Instagram, and Reddit usernames to your public key, which you store on the Keybase server. The important part is not just finding the key, but finding the right key. Normally using PGP you need to establish trust based on who signs each key. The problem is that if you’re e-mailing someone new, you won’t necessarily know if the people signing the key are fake. If you can link the key to established accounts of the user and cross-reference them with other accounts, then you have a fairly safe and easy want to confirm the owner of a key. The encryption scheme started with PGP, but is now evolving to include NaCl. The idea addresses a significant problem with public-key encryption, but doesn’t fully remove the ease-of-use problem most people have with encryption. Hopefully those are also being addressed.
All of these efforts are great, but they’re not solutions most people will use – yet. In the mean time, the question is how accessible are your e-mails to snooping. While the latest whiz-bang e-mail applications support IMAP and storing e-mails on the server, most have left POP behind. It is possible to download all your e-mails locally using IMAP, and then delete them all from your server, but it’s not the default. Next time another web site is hacked (don’t forget to check your e-mail address on HaveIBeenPwned.com) or another revelation about government snooping is revealed, you might wonder if storing everything locally, like POP does by default, might not be the better way to go.