
First of all, if what’s written above is your password, you need to change it now. I’ll wait. Okay, good, now for the rest of the article.
Why Passwords Don’t Work
It’s not much of a secret that passwords are not a very good way to secure information. The real problem is when companies try to make users utilize more secure passwords, they end up making the whole system less secure. Does that seem counterintuitive? Here’s a scenario. A company wants to make their corporate systems more secure. They decide that the passwords their employees are using are not secure enough, so they institute rules for passwords, which include:
- Must be 8 characters or longer
- Must include a lowercase letter
- Must include an uppercase letter
- Must include a number
- Must include a non-letter/number character
- Must not be the same as the previous password used
- Must not be the same as the username, or contain the username
You’ve probably run across these rules before. You may not have seen all of them, but you’ve probably seen most of them, and probably many of them with a single system. In theory, these are all good rules. Where they lead to a less secure system is that most people can’t remember a password that meets all those requirements. Did I make the first letter uppercase? or the last? Did I replace the O with a zero, or the A with an @? or both? Since some sites have different requirements, you end up with different passwords.
Take a look at Apple’s requirements for selecting a password for an Apple ID (which is used for everything from the iTunes Store to their iCloud e-mail accounts, etc.):
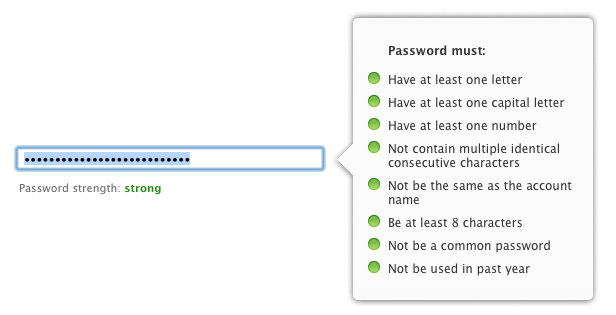
Originally the only requirement most sites had was that you had to have 8 characters. People generally can’t remember random 8 character passwords, so they use words they can remember, perhaps with some modifications. Introduce a requirement like a number and people need to change what they’ve been using. Perhaps one site has a number requirement and another does not, human nature leads one to use the same password with the only difference being the number. Now add in all the other requirements, and all of the sudden people are using many variations of their original password. When different sites have different requirements, people start getting confused and need to send themselves password reminders on sites they don’t use often.
Of course, a user should be using the most secure password they can, but the reality is simply that people use whatever is easiest to remember. If they can’t remember their password, they write it down. Or put it in their cell phone address book. Or keep a file on their computer listing all their passwords. The fact that someone has now put their secure password in an insecure location completely destroys the whole security system. Now instead of having a less secure password that the person could remember, you have a more secure password that is written down under the user’s keyboard at their desk, on a piece of paper in their wallet, or sitting in a text file on their computer.
PIN Codes
Another simpler look at this problem is PIN codes. When I lived in the US and opened bank accounts there, the bank teller would always let me enter a PIN code into a number pad so I could choose my PIN code without having to tell it to the bank teller. In Israel, my experience has been that I haven’t been able to choose a PIN code, and have instead been given a printout (using a special envelope that allows a PIN to be printed without being seen) where I need to use the PIN code that was assigned by the bank. So what’s more secure, the PIN I chose using the number pad, or the one assigned randomly by the bank? You might think the randomly assigned one, since it can’t be guessed using knowledge about me. Imagine how many people use their birthday as their PIN code (which by the way, if you do, you should change your PIN).
So the randomly assigned is more secure, right? Well, no. Since people have no reference to remember a random number, they tend to write it down or put it in their phone somewhere. You might think you can easily remember a four digit number, but what if you have multiple accounts? All with random PIN codes. I would say, therefore, that as long as you don’t choose an easily determined PIN code, being able to choose one is probably more secure.
The long-known solution to these problems is that there needs to be second piece of information in addition to your password which needs to be given in addition to your password, this second piece of information is what gives the name two-factor authentication its name. Bank machines have always had two-factor authentication – you need a physical bank card and you need to known your PIN.
With online two-factor authentication, what the second piece of information is gets complicated.
Hardware Code Generators

One of the first practical solutions to two-factor authentication was to introduce hardware code generators. If you’ve worked in high-security locations like financial institutions, military contractors, government offices, etc. it’s likely you’ve seen some form of code generator.
The RSA SecureID token is one of the more common physical code generators, and has been around for just less than 20 years as far as I can remember. A small dongle intended to fit on your keyring, it generates a numeric code that changes based on the time. At any given time, when logging in to a secure service, you would enter your password and the number given on the screen at that moment. The hardware token is tamper-proof, meaning that if you try to open it up to examine it, it would break and not work anymore. The great thing about these kind of code generators is that there is no need to be connected to a network, they just work based on the current time.
The fact that the SecurID tokens and their like were tamper-proof is evidence of one of their vulnerabilities – they are based on a secret which if known makes them completely insecure. This became evident back in 2011 when RSA itself was hacked, leading to tens of millions of SecurID tokens having to be replaced. Lockheed Martin, the military contractor responsible for some of the US military’s most important defense systems like the F-35 fighter jet, Trident missiles, satellites, etc. was hacked shortly after the RSA hack, before the compromised tokens could be replaced (and perhaps before the extent of the RSA breach was known, or at least known to Lockheed Martin).

There are other hardware solutions besides stand-alone code generating tokens. One interesting example is the YubiKey. It is not that different from a security point of view as the SecurID token. The difference is that it has no screen, no battery, and doesn’t work by itself. Instead, it plugs into your computer using USB (or to your mobile device using NFC with one model) and using software on your computer and servers online, generates the unique password used for authentication. Some are special made for specific services, and some are more general-purpose. Some can even be configured to output a static password as if it was a USB keyboard. A good summary of the technical details of the Yubikey can be found on their web site. The big advantage of the YubiKey is it’s small, has no maintenance needed (no battery), and it’s cheap ($25 for the basic model).
Software Code Generators

While hardware tokens have been around for a long time, nowadays when so many people carry around smartphones, it has been possible to create software-based code generators. RSA in fact offers SecurID software apps for most major mobile operating systems, including iOS, Android, Blackberry, Blackberry 10, Windows Mobile, Windows Phone, Symbian, etc. One of the advances available by having an always connected smartphone, however, is that there are now many more options available for software code generation. Indeed, many services provide their own software code generators within their smartphone apps.
As an example, Facebook’s mobile app has a code generator built in, which you can use with their two-factor authentication system which they call Login Approvals. I have a friend who enabled Facebook’s two-factor authentication last year, then got locked out of his account for months. Now when you sign up, they give you a week to shut it off just in case you end up locked out. They also let you print out up to ten codes you can use when you don’t have your phone. I guess you put that piece of paper in your wallet? It seems there’s a pattern here.
Two-factor authentication itself is not a panacea. It needs to exist within a larger framework of security that needs to be well though out. Dropbox, which offers two-factor authentication using one-time codes sent via SMS or via their mobile app, had their two-factor system completely bypassed by hackers who used a fake e-mail address and pretended they had lost their phones. It’s quite clever. Luckily for Dropbox, they contacted the company before publishing their exploit so it could be fixed. Not all hackers are so generous, however.
Biometrics to the rescue?
Some people believe that biometrics will be what replaces the use of passwords. People have believed that for decades. There are reasons it hasn’t happened yet, and reasons it’s unlikely to happen any time soon.

Biometrics is the use of unique physical body characteristics to verify your identity. The most well known biometric type in use is the fingerprint. Other biometric types include iris, retina, face, hand geometry, ear shape, gait, odor, speaker recognition, writing recognition, typing rhythm, etc. Not all of these are commercialized, but some like iris recognition and hand geometry are widespread. What is common to almost all of these biometric types, other than fingerprints, is that the hardware required to capture the biometric data is much too big to be used in a mobile device, too expensive, or too clunky from a user experience point-of-view. Some progress is occurring in allowing face recognition via the front-facing cameras in mobile phones, and possibly iris scanning, but things like odor and gait, ear shape, writing recognition, etc. are not coming to mobile any time soon. Without mobile, these technologies are really irrelevant in terms of password replacement.
There’s a reason fingerprints can’t really be used to replace a password, and I’ll get to that, but first let’s take a look at what you might think is fingerprints already in use for this purpose.
Touch ID and iCloud Keychain

You might be thinking to yourself that the iPhone 5S has Touch ID, so therefore fingerprint biometrics have made it into the mainstream of mobile authentication. Well, no. Touch ID is innovative in a lot of ways, and it can replace entering a pin to access your phone, but by itself it does not replace passwords (it does allow you to buy things from the iTunes Store and other Apple ID-connected stores, but that’s because it’s Apple and they themselves confirmed the phone is yours). Apple knows this, which is why it has been deploying iCloud Keychain into an increasing number of countries (over 100 countries now). You might not have even noticed iCloud Keychain, which was introduced with iOS 7.0.3 and OS X 10.9 just this past fall.
iCloud Keychain lets you sync passwords (as well as credit card details and Internet account info) via iCloud between your Apple devices such as your Mac, iPhone and/or iPad. When you go to login to a web site using Safari on your Mac or iOS device, it will ask you if you want to sync the password using iCloud Keychain. If you are registering for a new account on a web site, it will recommend a randomly generated password, which you will not need to remember (eliminating the paper taped under your keyboard problem), since it is synced between all your devices. You can of course choose your own password instead. Either way, if you want to save it to iCloud Keychain, it then becomes available for auto-fill on all of your devices.
What does iCloud Keychain have to do with biometrics and two-factor authentication? Let’s look at how you sign up for iCloud Keychain (and why it needed to be rolled out in specific countries). You turn on the feature, and authenticate using a mobile phone. This is not dissimilar to how the mobile messaging apps like WhatsApp verify your phone belongs to you (one of WhatsApp’s biggest expenses by the way). Once your phone is verified, it can be used as a verification device for your non-mobile devices such as your Mac (and I define mobile here as cellular-connected). Now that your mobile device is authenticated, all of your passwords stored in your iCloud Keychain are essentially secured with Touch ID (or a PIN code if you do not use it). Strictly speaking, this is not two-factor authentication. The web site you’re connecting to using the username and password stored in iCloud Keychain has no idea that in order to enter that password you had to authenticate your phone via SMS, and then access it using your fingerprint. If your password is found by someone, by hacking or otherwise, the fact that your use a fingerprint scanner on your iPhone does not effect that fact that they can access the web site without your phone.
The problem with fingerprints

In general, fingerprints are a great way to verify your identity. There are some people that have unreadable fingerprints (for a variety of reasons) but they are small in number. Fingerprints can also be faked – you might remember that Touch ID itself was circumvented with a fake fingerprint just two days after being released. Two days! Those issues aside, fingerprint biometrics is a fairly well researched technology, and the person who would want to fake your fingerprint would need both a copy of your fingerprint and access to your phone.
The big problem with fingerprints, like all biometric traits, is that once they are compromised there is no going back. If your fingerprint is copied, that’s it, end of game. Sure some fingerprint scanners try to scan under the skin to prove the fingerprint is on a living person, etc. but Touch ID also claimed that capability, and that turned out to be false.
In order to prevent losing the ability to use one of your biometric traits, a considerable amount of research has gone into developing a way to mix the benefits of biometrics and cryptography. This research has led to techniques allowing you to create a password that is based on your biometric trait, but cannot be reversed to reveal your biometric trait. Additionally, you can generate an unlimited number of these passwords, allowing you to change your biometric-based password just like you would change your regular password. This is called ‘revocable biometrics’ and it uses a variety of techniques such as fuzzy extractors. It’s a complicated area, but one thing which has been found in the extensive academic research is that a single fingerprint doesn’t contain enough data to create a secure revocable password. In other words, you will never be able to use a single fingerprint to create a secure password that cannot be hacked (at least with current mathematical and biometric understanding).
So where does that leave us?
At the moment, I’d say we’re pretty much in the same place we were 20 years ago as far as password security. That’s not to say there hasn’t been progress. It is cheaper to implement two-factor security. Dedicated hardware is no longer required. Two-factor security is available to almost any company, although foolproof implementation remains difficult, as evidenced by the RSA and Dropbox hacking events.

That said, there do seem to be some interesting products on the horizon. A company named Nymi has come out with a bracelet that uses your heartbeat to authenticate your identity. That’s an interesting trick, because authenticating via a wristband means that the technology can be integrated into any number of fitness bands and smart watches that people are already going to be wearing. I don’t think the concept of a stand-alone band like the Nymi has a long term success possibility, but the concept is interesting as a feature of other products. Not too surprisingly, it turns out Apple has several patents on a very similar feature going back to at least 2009. I tweeted a few weeks ago that if Nymi had good IP, they’d be an obvious purchase for Apple, but considering Apple’s patent portfolio maybe there’s no need to buy them. Even if their IP is weak and Apple could sue them into oblivion, if their product is further along than whatever Apple has developed, it’s still possible Apple could buy them, but they’ll have a much worse negotiating stance.
A company called EyeLock introduced a hockey-puck sized Iris sensor at CES earlier this year, called the myris. It connects via USB to your computer and lets you authenticate using your Iris, raising the false-positive rate from the 1 in 50K of a fingerprint to somewhere above 1 in 1 and a 1/2 trillion. Their next goal is to integrate this into the body of laptops and monitors, and eventually mobile devices. They claim to be able to detect that the eyes belong to a real living person (and not a photo, or on the end of a pen if you remember Demolition Man) which if true would be important for such technology. Certainly many biometric systems have been circumvented. It seems this technology is far from being usable in a mobile device, however, so this is years away from being practical.
At the Mobile World Congress (MWC) in Barcelona last week, a Chinese company called YunTab was pushing it’s $152 YunTab S5 smartphone that had one unique feature – 3D facial recognition for unlocking the phone. The phone uses two infrared emitters and an extra infrared camera to create a 3D image of your face for authentication. It’s an interesting implementation of facial recognition, considering that other implementations have circumvented by pointing the camera at a photo or video. I don’t think you’ll see this phone taking over the market (it’s only available in China right now) although it’s not a bad deal for an Android phone with okay specifications.
This is an area Apple also has extensive intellectual property. Apple bought Swedish facial recognition company Polar Rose in 2010. Apple also bought Israeli 3D sensor company PrimeSense (the company behind the original Xbox Kinect motion sensors) in 2013. Putting aside motion sensing, the technology is very similar to what the Chinese company is using to build a 3D model, and in fact PrimeSense had filed a patent on enhanced facial detection using depth before Apple purchased them. PrimeSense isn’t the only Apple acquisition with very similar patents. Authentec, which Apple purchased in 2012 and who is better known for the technology behind Touch ID, also had patent applications related to 3D facial recognition. Lastly, Apple has patents of its own in facial recognition, including using 3D information. I bring up the Apple connection again because I think the issue of authentication using biometrics is important, and in the end you will have a device with you that will be verified as yours (a la iCloud Keychain) and that you will be using biometrics to secure it. Apple is likely to be one of the companies making the devices you will use for this purpose.
Where are we heading? We’re heading beyond two-factor authentication to, you guessed it, three-factor authentication. Those factors are what-you-know (a password), what-you-have (your device), and who-you-are (a biometric sample). We need all of these factors, because without any one of them, the others have a much higher failure rate. The key is making them simple to use. Making them simple to use means integrating everything into a single device that you always have with you. Whatever that device, it needs to be able to be authenticated as yours (such as via SMS), needs to be able to securely store your biometric hash, and needs to be able to read your biometric signature. Right now the only device that fits that description is a smartphone, and just barely. I believe much of these functions will be in fact pushed to a wearable device. One reason it needs to be wearable is for security reasons – you’re less likely to lose your watch than your phone. Wearables are certainly on the rise now, and I think you will see many more of them integrating security functionality into them (like the Nymi). What else will wearables be integrating? That’s in my next article…



Pingback: Who do you trust with your identity? | off on a tangent
Pingback: One Wearable to Rule Them All? Not likely. | off on a tangent